Gsuite login to AWS Organisation
How to setup gsuite Saml login for multiple aws accounts

Every company eventually sets up multiple AWS accounts. Managing IAM users and passwords in each of them becomes painful for both administrators and employees over time. We want to leverage setup Gsuite Authentication (SAML) to an AWS Organisation with multiple accounts.
Steps to follow (Assuming root/admin access on both Gsuite and AWS):
Login to AWS root account:
Enable SSO from here: https://console.aws.amazon.com/singlesignon/home?region=us-east-1#/dashboard
Go to settings and change Identity source to External Identity Provider.
Take the values of Service Metadata. We'll need them in next step.
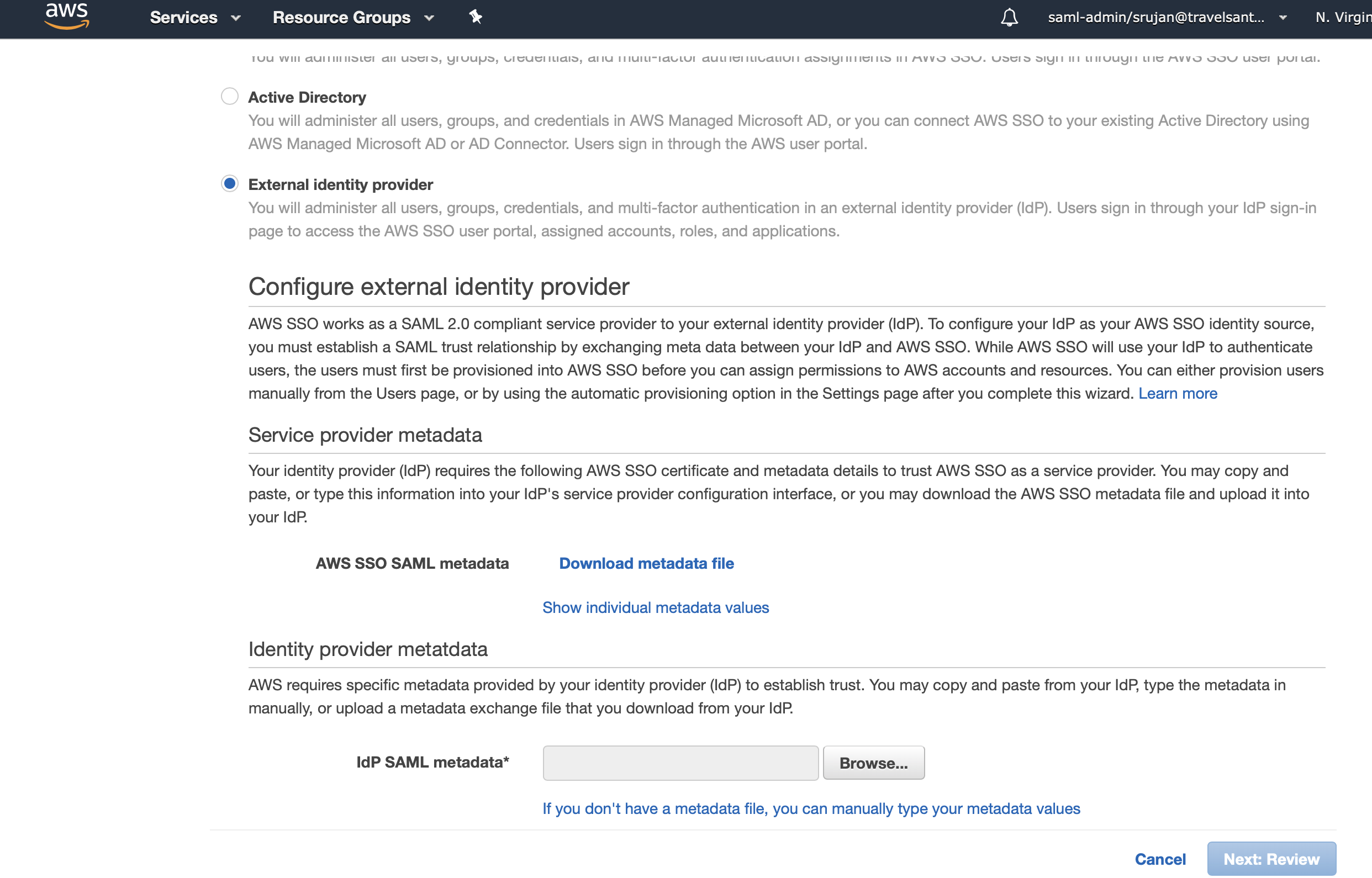
Copy the values from "Show individual Metadata values".
Login to G-Suite:
- Use the above values and create a SAML app here:
Set Up custom app.
https://admin.google.com/<our_domain>/AdminHome?hl=en_GB#AppsList:serviceType=SAML_APPS - Download IDP metadata.
- Give it some name such as AWS-Login, that we can recognise with.
- Add the details from above here:
Add ACS url as ACS url; Issuer url as Entity ID; Sign-in URL as StartURL; Leave others to be default values.
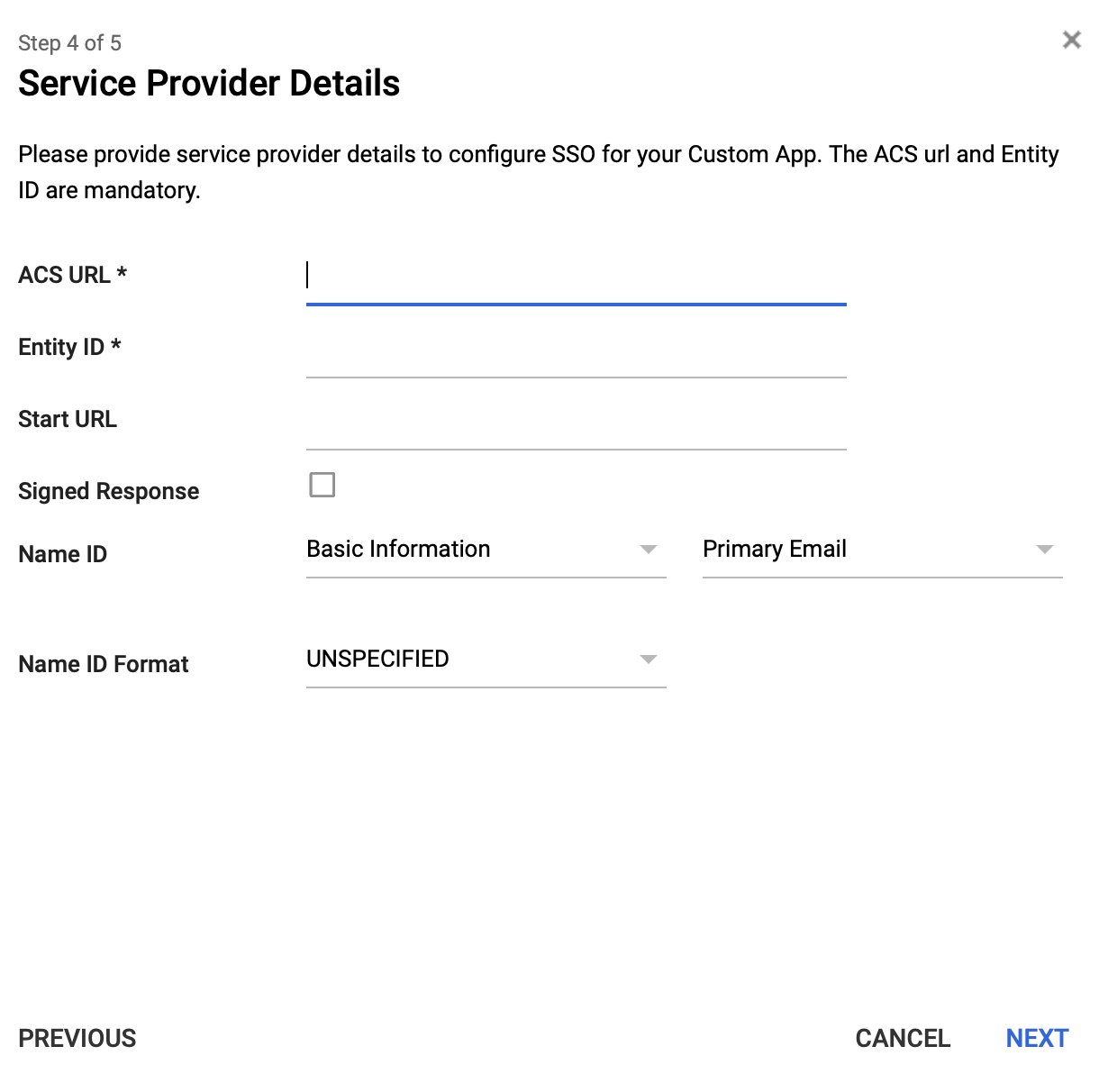
-
Leave all attribute mappings as is. Click on finish.
-
Enable app for all users. We'll manage their permissions via AWS.
Back to AWS:
- Upload metadata in above page and click on next.. we should see a page like this.. do read and review all those things. Don't ignore them like terms and conditions ;)
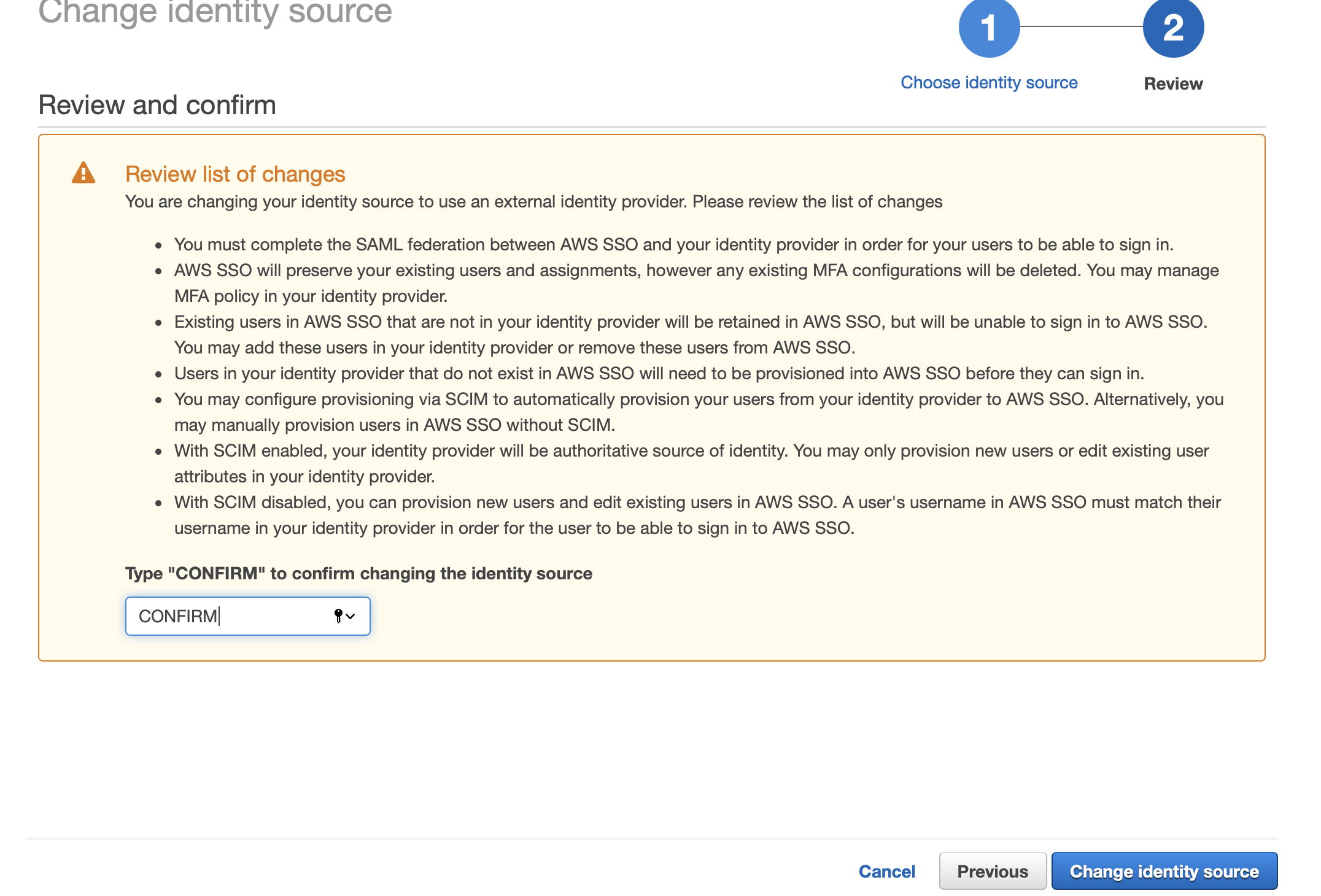
- Save the settings.
Do not close this tab.
- Return to settings page. Add users, groups, accounts, etc.
Google doesn't support SCIM provisoning of users. Hence, we've to create users manually.
Note: Both Username and Email address fields should've email ID in its value, as we setup NameID to Email when we setup SAML app in gsuite earlier.
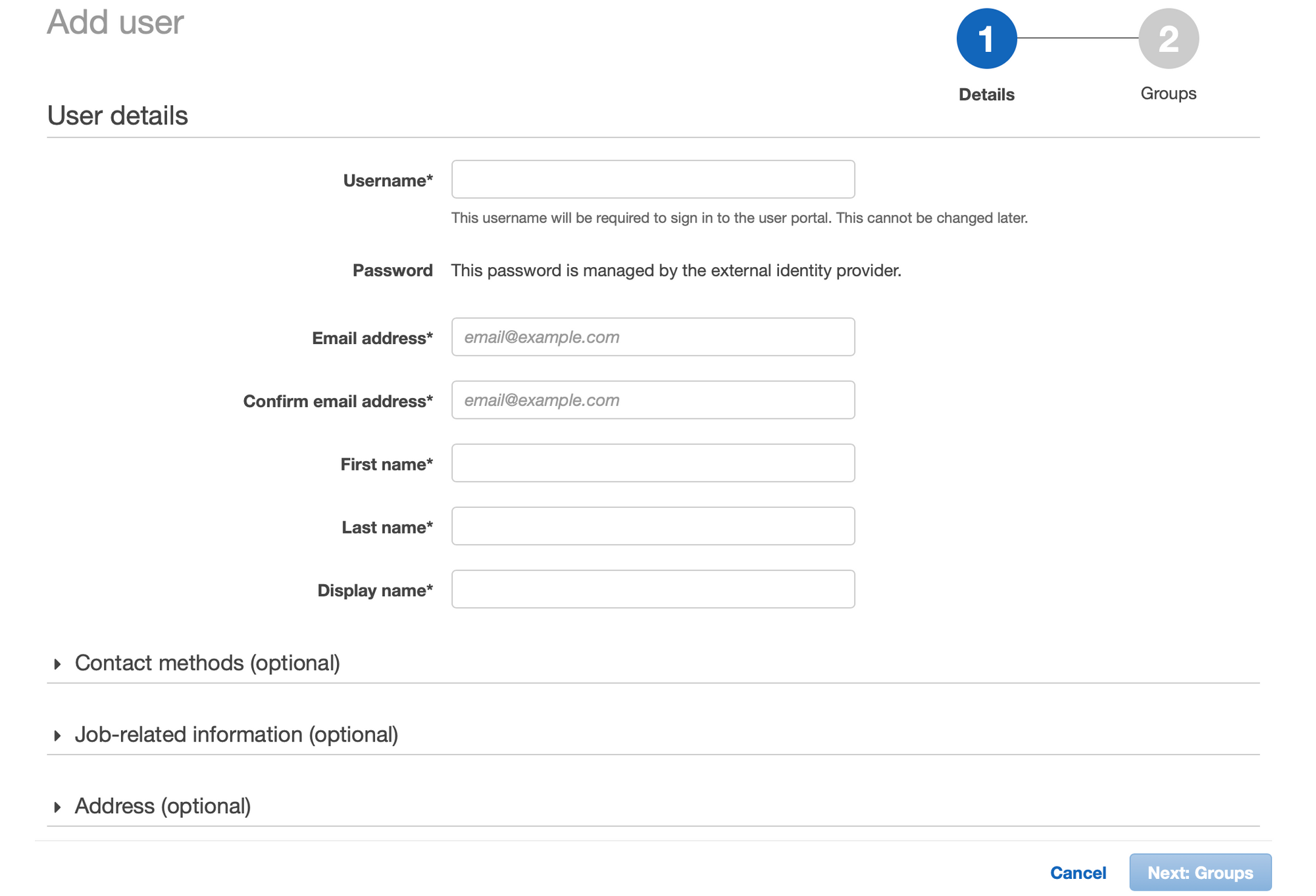
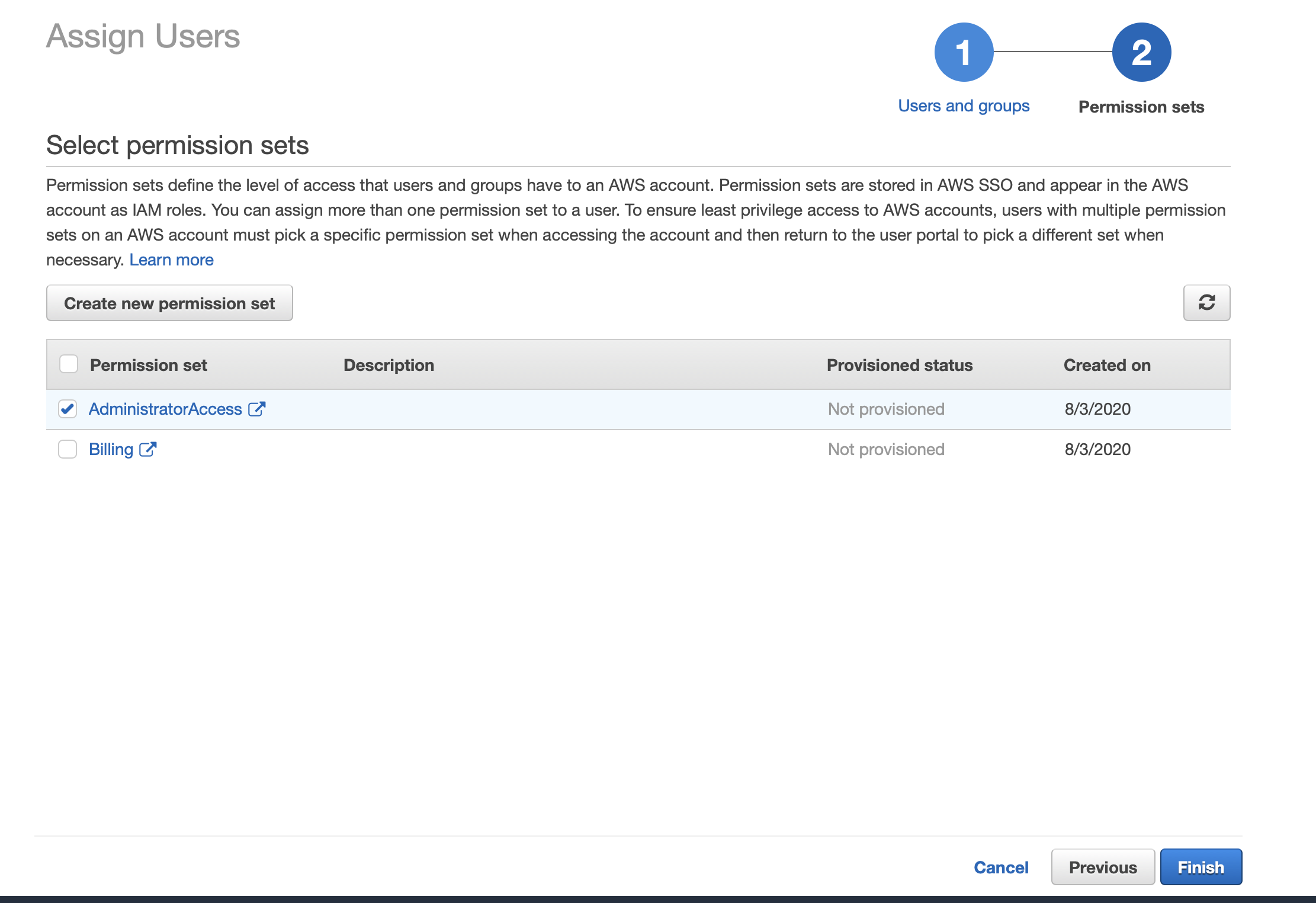
- Once we created user, let's create permission sets. For the sake of this blog post, I'll setup Administrator access and Billing permission set.
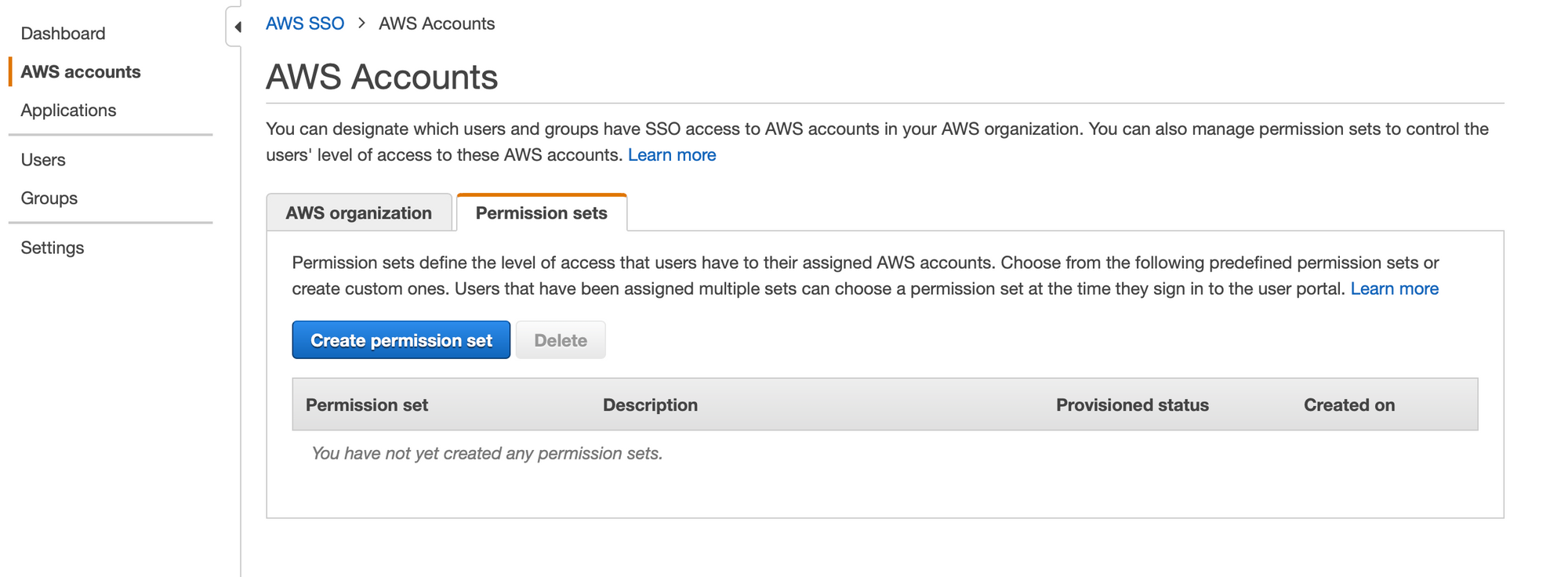
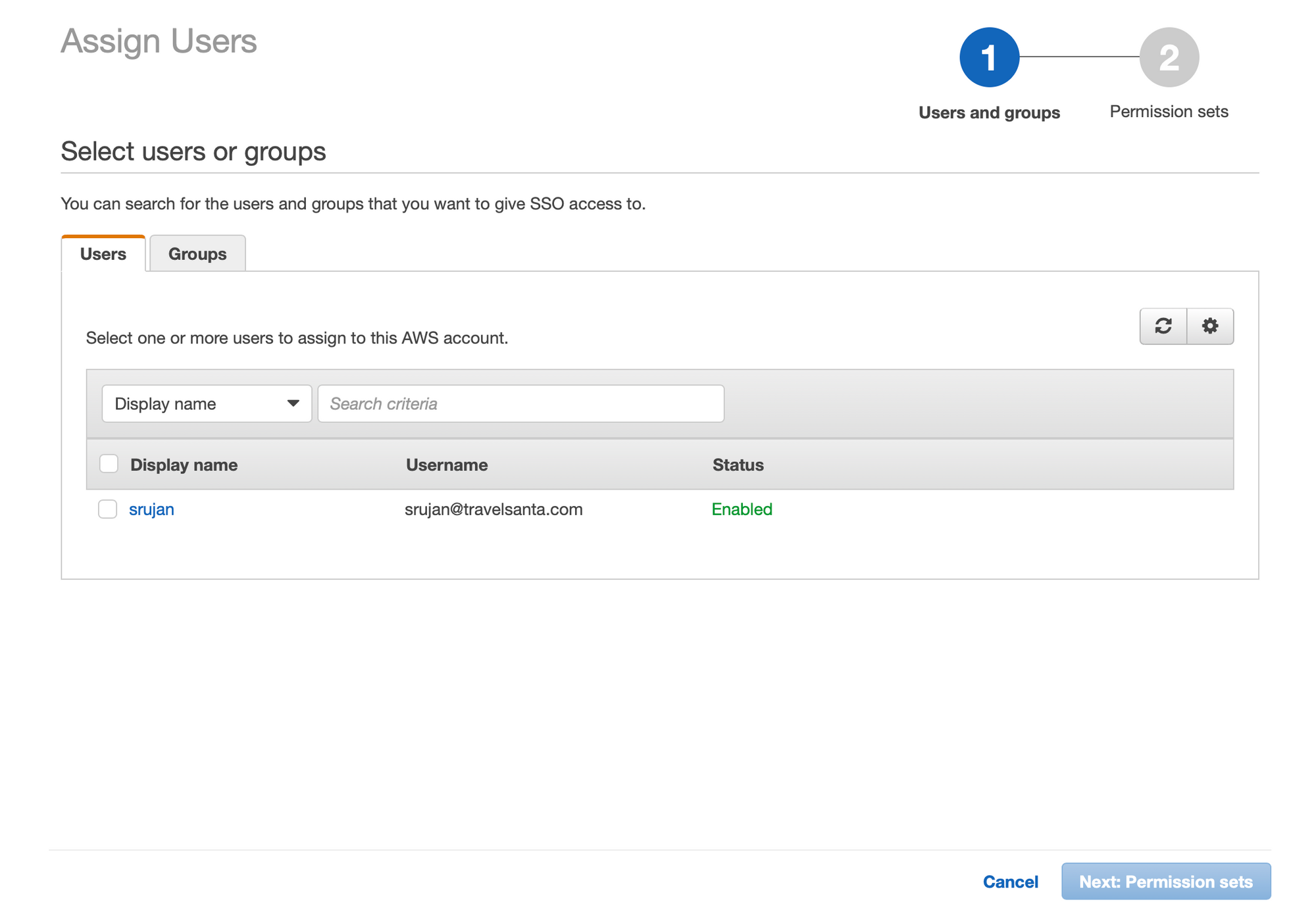
- Now, Go to accounts tab again.. select an account. Click on
Assign Users, select desired permission sets for the user.
- Go to Dashboard tab: Change the user portal to company friendly name.
Hit the url in an incognito and login to see multiple accounts displayed. Select the desired account and enter the dashboard.
For cli access with SSO:
- Run
aws configure sso, enter above URL and region asus-east-1. It should open a browser and verify itself. In case of server with no browser, it'll display a URL and a code to verify.
Further reading/references:
- For aws sso cli, https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-sso.html
- For IDP, https://docs.aws.amazon.com/singlesignon/latest/userguide/manage-your-identity-source-idp.html
Hope this is helpful. Questions/Comments/Feedback welcome on twitter https://twitter.com/acsrujan or mail me at [email protected].


